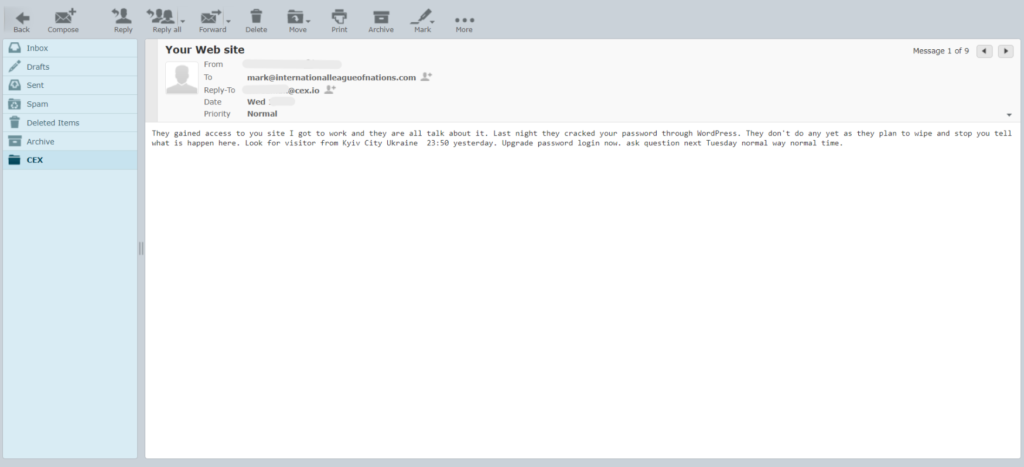
For the past two months, the International League of Nations (ILON) has been under a persistent cyber assault. The attacks, which originated from IP addresses in Kyiv, Ukraine, and occasionally Bulgaria, were relentless in their attempts to breach our website. After weeks of fending off these intrusions, the attackers finally succeeded on the night of September 10th at 11:50 pm. While we initially suspected external actors, it soon became clear that the orchestrators were far closer to the subject of our ongoing investigation than we first believed.
Thanks to an insider who has been working with us during our investigation, we now know that actors within the cryptocurrency exchange CEX.IO were behind these cyberattacks. This revelation comes at a critical juncture in our four-month investigation into the company’s alleged misconduct, adding a new, darker dimension to their already questionable practices. The attacks coincided directly with our requests for comment from CEX.IO, further cementing the fact that these were not random hacking attempts but a deliberate effort to silence us.
Coordinated Attacks and the CEX.IO Connection
For two months, we had been aware of repeated hacking attempts on our website. While we took each of these threats seriously, they initially appeared to be standard cyber probes—attempts to find vulnerabilities without any particular agenda. However, it quickly became clear that this was no ordinary cyberattack. The IP addresses responsible for these attacks were traced to Kyiv, Ukraine, a location linked to key figures within CEX.IO. Given our ongoing investigation into CEX.IO’s operations and the increasing pressure we were applying, the connection between the attacks and our investigation became impossible to ignore.
The most damning evidence came from within CEX.IO itself. Our insider contacted us, confirming what we had begun to suspect: CEX.IO was orchestrating the cyberattacks. The tip-off came the following morning after the most significant breach on September 10th. According to our source, the company’s leadership was fully aware of the hacking efforts, which were designed to disrupt our investigation and prevent the release of damaging information.
This insider testimony is more than just circumstantial. It directly links the timing of the cyberattacks to key moments in our investigation.
On multiple occasions, we were in communication with CEX.IO representatives who, at the same time, were attempting to access our website through unauthorized channels. The insider detailed how CEX.IO’s management had become increasingly frustrated with our line of questioning and the mounting evidence of their regulatory violations. Instead of addressing these concerns openly, they chose to retaliate through underhanded tactics.
The September 10th Breach: A Calculated Move
The breach on September 10th was not an isolated event. It was the culmination of weeks of planning and repeated attempts to compromise our systems. At precisely 11:50 pm, the hackers exploited a vulnerability that allowed them access to sensitive areas of our website. This occurred as we were finalizing an article that revealed critical findings about CEX.IO’s operations, including their deceptive practices, questionable regulatory status, and offshore ties.
Thanks to the insider’s tip, we were able to take immediate action and minimize the damage. However, the breach was a wake-up call—a clear indication that CEX.IO was willing to go to extreme lengths to protect itself. The timing of the attack, coupled with the information provided by our source, confirms that this was not a random act of cybercrime but a targeted effort to suppress the truth.
A New Layer of Deception: CEX.IO’s Hidden Agenda
This revelation adds a new and disturbing layer to our investigation. For months, we have been uncovering evidence of CEX.IO’s unethical practices, including misleading investors about their regulatory status and hiding the true ownership of their offshore entities. Now, it seems that the company is not only deceiving its customers but also actively attempting to sabotage independent investigations into its activities.
The insider confirmed that CEX.IO’s management was particularly alarmed by the direction of our investigation and had resorted to desperate measures to prevent the publication of our findings. This included not only cyberattacks but also attempts to mislead us through selective disclosure of information and evasive responses to our questions. The fact that they resorted to hacking, rather than addressing these issues transparently, speaks volumes about the company’s true character.
The Insider’s Warning: What Comes Next
Our insider’s warning was crucial in mitigating the damage from the September 10th breach, but it also provided us with critical insight into what we can expect moving forward. According to our source, CEX.IO’s leadership is aware of the damaging nature of our findings and is prepared to take further action to protect itself. This includes not only continued cyberattacks but also potential legal action or smear campaigns designed to discredit our organization.
In response to these threats, we have significantly upgraded the security of our website. We have implemented new firewalls, tightened password protocols, and installed advanced monitoring systems to detect any further attempts to compromise our systems. While we are prepared for future attacks, we remain resolute in our commitment to uncovering the truth about CEX.IO’s operations.
CEX.IO’s Leadership: A Web of Deceit
Throughout our investigation, one of the most troubling aspects has been the apparent disconnect between CEX.IO’s public-facing image and its behind-the-scenes actions. The company presents itself as a legitimate, trustworthy platform for cryptocurrency trading, but our findings suggest otherwise. From misleading claims about regulatory compliance to offshore dealings, CEX.IO has consistently prioritized profit over transparency.
The insider’s revelations about the cyberattacks only serve to reinforce this pattern of deception. Rather than engaging in a good-faith dialogue with ILON, CEX.IO’s leadership has chosen to operate in the shadows, attempting to cover their tracks through digital sabotage. This is not the behaviour of a company that has nothing to hide.
The Link Between CEX.IO and Ukrainian Hackers
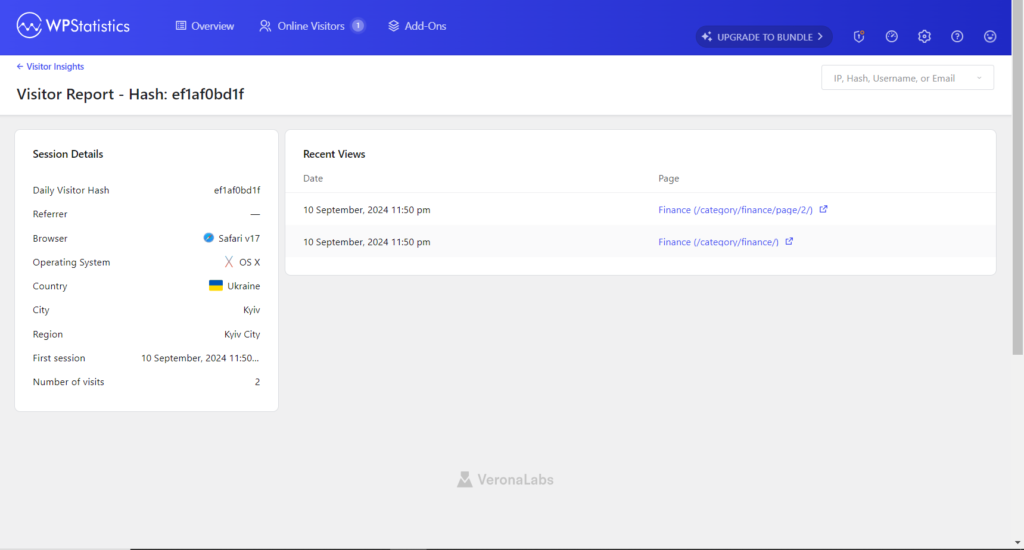
One of the most concerning revelations from our investigation is the link between CEX.IO and cyber actors based in Ukraine. Our insider has confirmed that the hack came from within the CEX.IO office the same geographical region as key members of CEX.IO’s leadership team.
Ukraine has long been known as a hotbed for cybercrime, with numerous hacking groups operating within its borders. Given CEX.IO’s deep ties to the region, it is not beyond reason to suggest that they may have leveraged these resources to carry out the attacks on our website. This would not only implicate CEX.IO in cybercrime but also raise serious questions about the ethical standards of its leadership.
Upgrading Security: Preparing for the Future
In the wake of the September 10th breach, ILON has taken extensive measures to fortify its digital infrastructure. We are now better prepared than ever to withstand further attacks, and our new security protocols will ensure that any future hacking attempts are swiftly detected and neutralized. Our investigation into CEX.IO will continue, undeterred by their efforts to silence us.
We have also taken steps to safeguard our sensitive information, ensuring that no data was compromised during the breach. Our team remains committed to transparency, and we will not allow these underhanded tactics to deter us from exposing the truth.
In the after Marth of the breach
In an exchange with Joel Kosloski, CAMS-RMCIO & CISO at CEX.IO US. Mark sharply calls out Joel for his continued lack of action and transparency regarding the unresolved issue of the missing 2.434 BTC and the hack on the International League of Nations (ILON) website. Mark highlights a key point: the insider email that tipped off ILON about the cyberattack and the precise data showing the location and time of the hack (Kyiv, Ukraine, 10th September, 11:50 PM) were both shared with Joel. Despite the clear evidence presented, Joel chose not to comment or address these specific details.
Instead of acknowledging the gravity of the situation or providing any meaningful response, Joel’s silence further confirmed CEX.IO’s involvement in the cyberattack. Mark emphasizes that Joel’s failure to even acknowledge the evidence provided – particularly the email from the insider and the supporting data – reveals a troubling pattern of evasiveness.
This inaction only deepens Mark’s resolve to hold CEX.IO accountable, as before Joel has never been able to supply an explanation for the missing 2.434 BTC, instead, he has a faceless person just comment “I could not locate the mentioned amount of 2.384 BTC in your account.” Mind you they could not even get the amount correct how are they supposed to ensure it is safe
Mark makes it clear that CEX.IO’s repeated failure to return the missing funds, coupled with their involvement in the hack, indicates that the company is acting as if it is above the law.
Joel has not has not responded to the clear-cut evidence supplied to him.
We also reached out to numerous members of management to no avail.
The Investigation Marches On
Despite CEX.IO’s efforts to undermine our work, the investigation is far from over. In fact, the recent cyberattacks have only strengthened our resolve to uncover the full extent of their wrongdoing. Over the past few months, we have compiled substantial evidence of CEX.IO’s unethical practices, and we are now preparing to release a comprehensive report on our findings.
This report will be shared with regulatory authorities and the public alike. We believe that it is in the public interest to know the true nature of CEX.IO’s operations, and we will not be silenced by cyberattacks or intimidation tactics.
A Call for Accountability
The time has come for CEX.IO’s leadership to face the consequences of their actions. Their attempts to sabotage our investigation, coupled with their misleading statements to investors and the public, demonstrate a clear disregard for transparency and accountability. We urge regulators in all relevant jurisdictions to take a closer look at CEX.IO’s activities and hold them accountable for their misconduct.
As for ILON, we will continue to do what we do best: shine a light on the truth, no matter how deeply it is buried. The cyberattacks may have temporarily slowed us down, but they will not stop us. CEX.IO’s attempts to cover up its actions have only fuelled our determination to expose the full extent of its deceit.
The truth will come out. It always does. And when it does, those responsible will have to answer for their actions.





